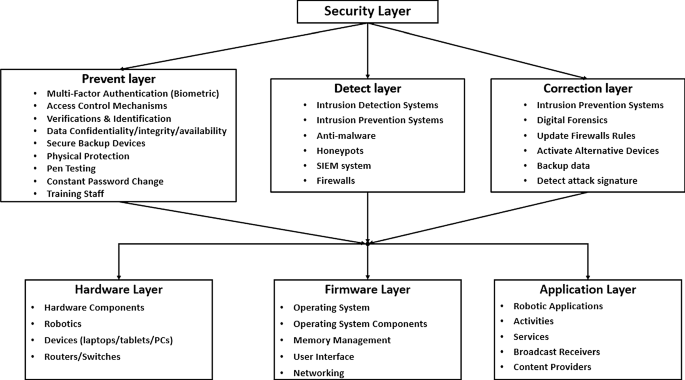
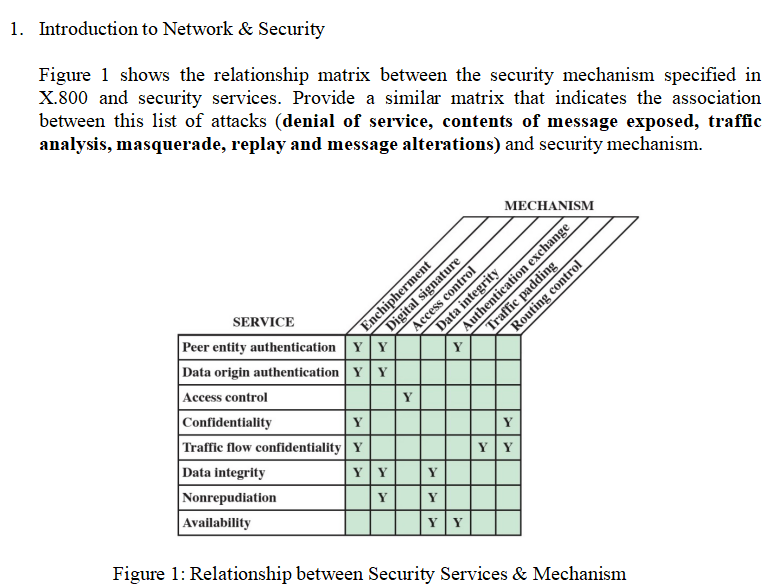
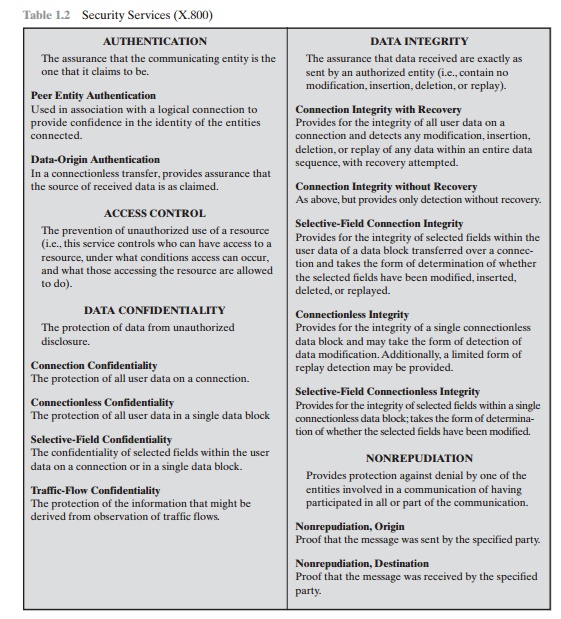
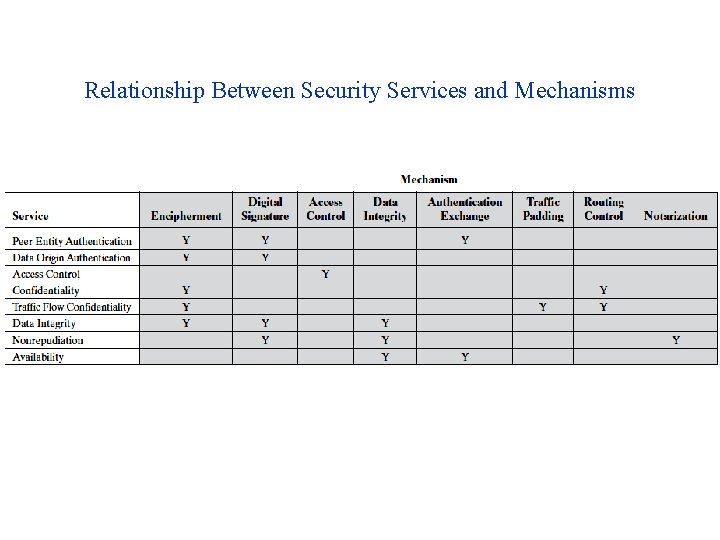
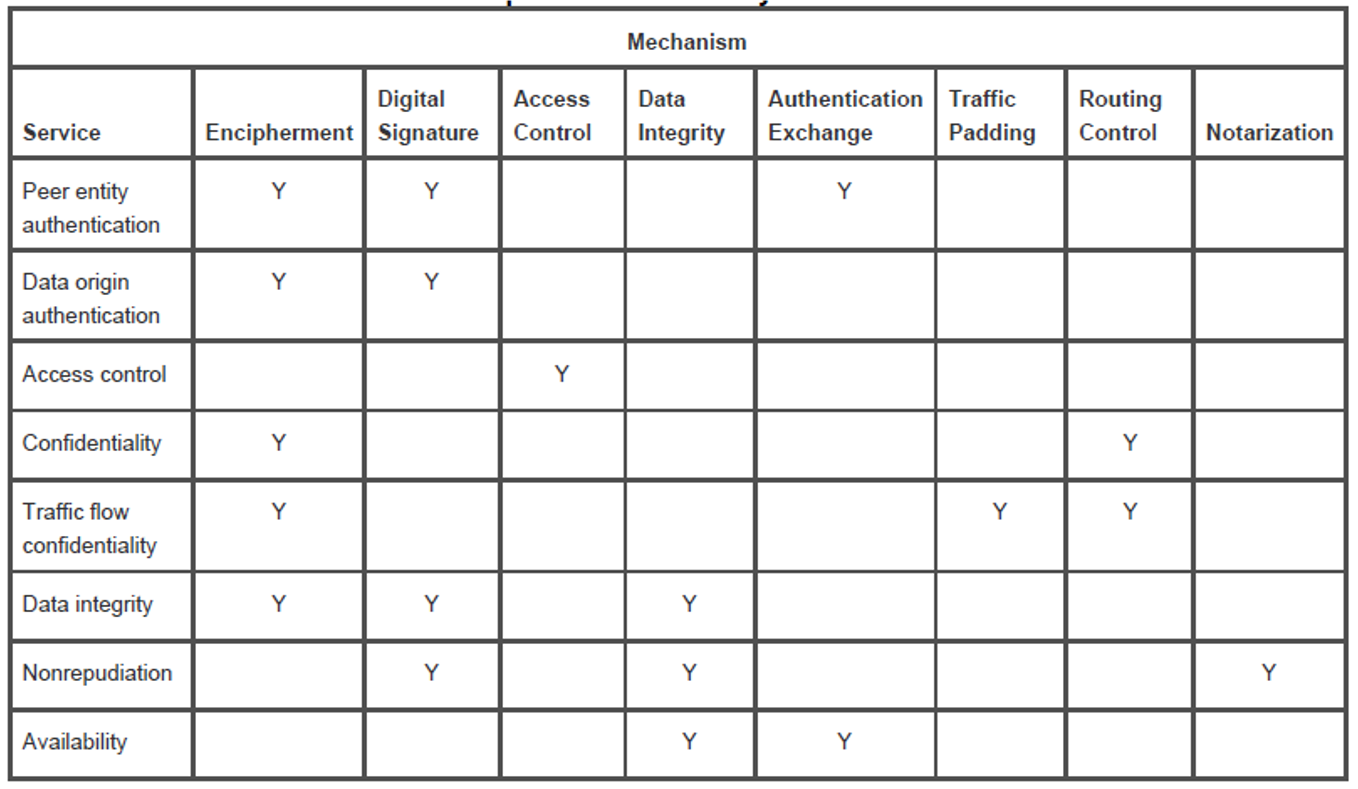
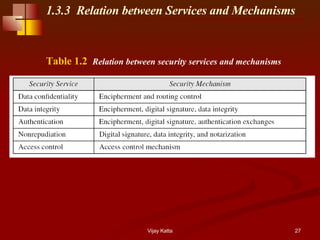
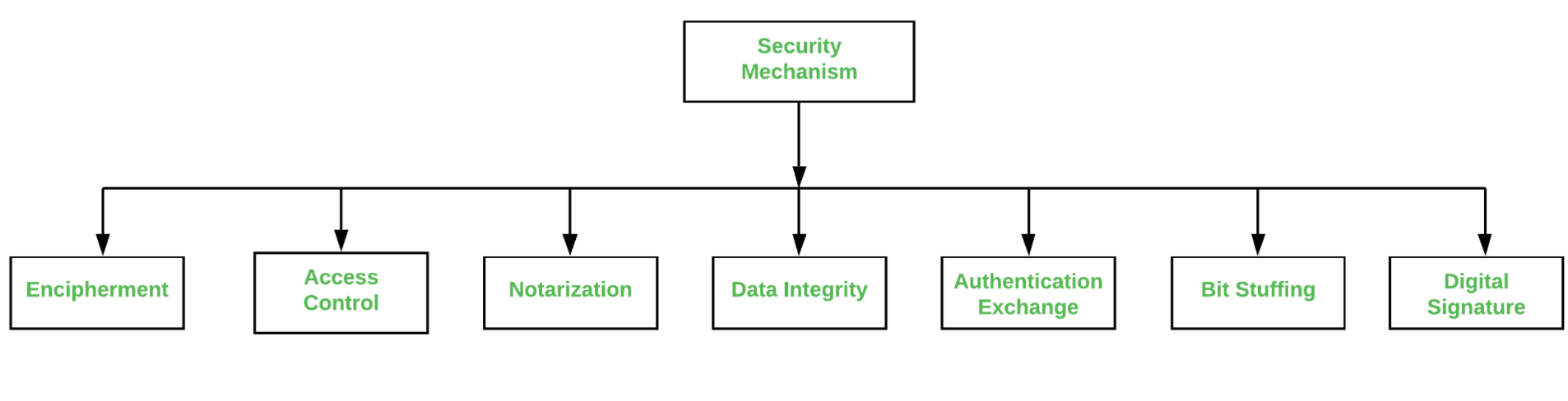
CryptographyBhutan - Lesson 12 #securitymechanism #securityservices Security services are implemented by a security mechanism or combination of mechanisms: 1. Peer entity authentication service can be implemented by or combination of Encipherment, Digital
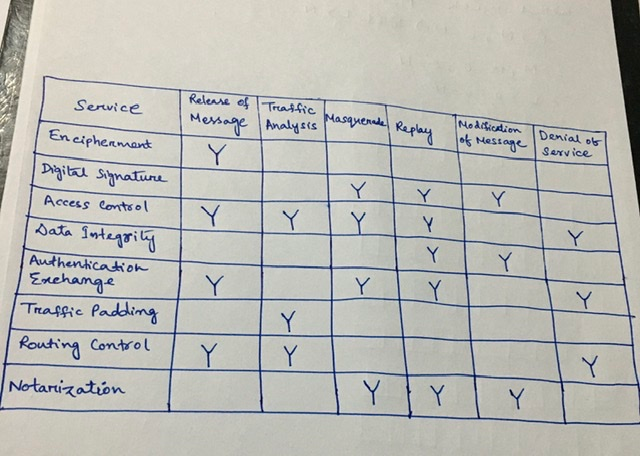
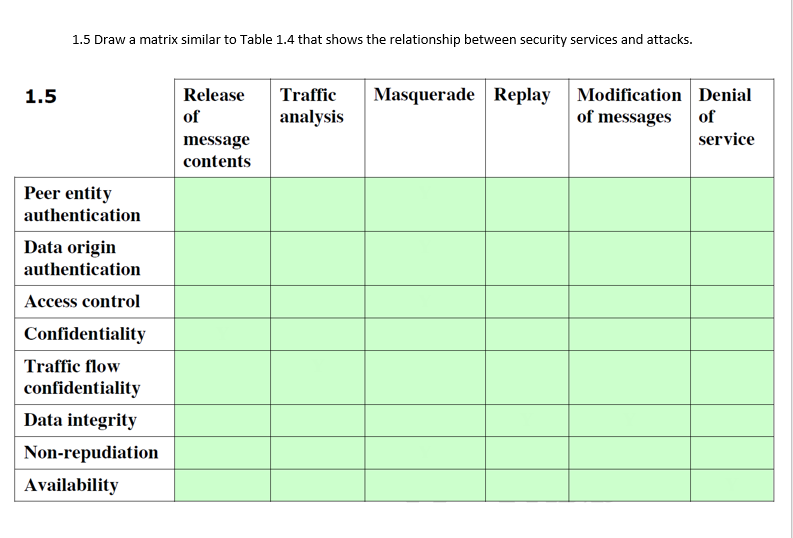
Solved) : Draw Matrix Similar Table 14 Shows Relationship Security Mechanisms Attacks Q42415984 . . . • CourseHigh Grades
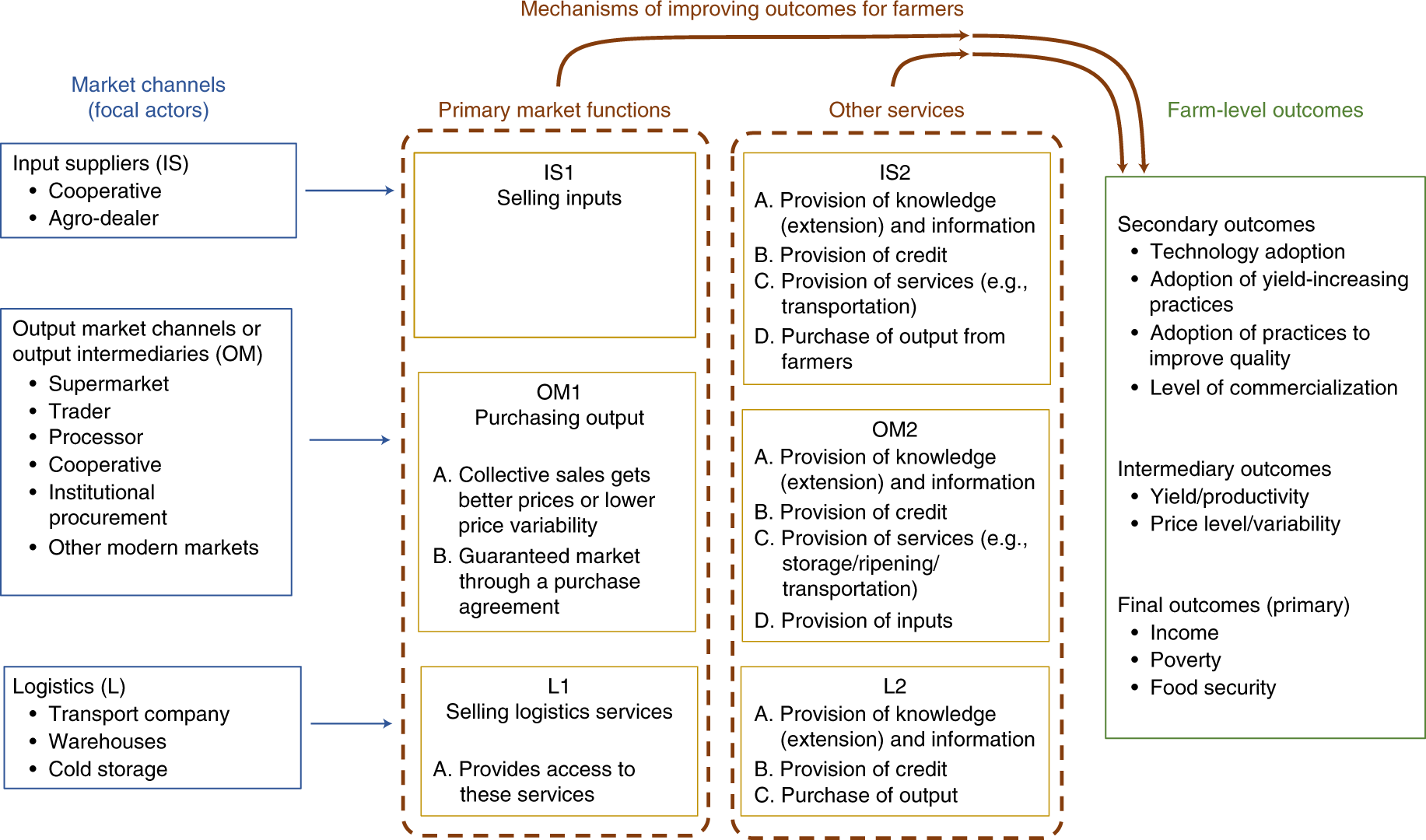
A scoping review of market links between value chain actors and small-scale producers in developing regions | Nature Sustainability
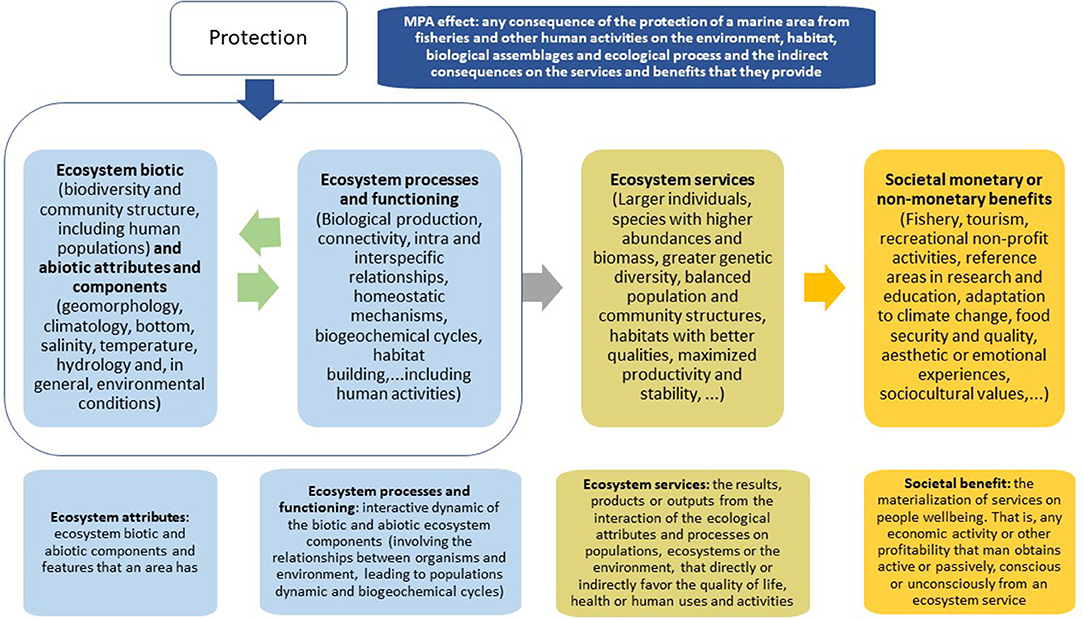
Frontiers | Reviewing the Ecosystem Services, Societal Goods, and Benefits of Marine Protected Areas | Marine Science
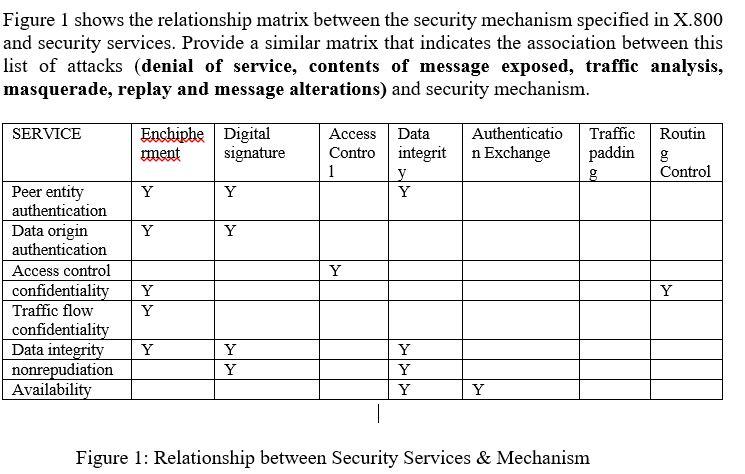
Network security essentials - chapter 1 - 7 Draw a matrix similar to Table 1.4 that shows the relationship between security services and | Course Hero

Table 3 from Trusted third party services for deploying secure telemedical applications over the WWW | Semantic Scholar
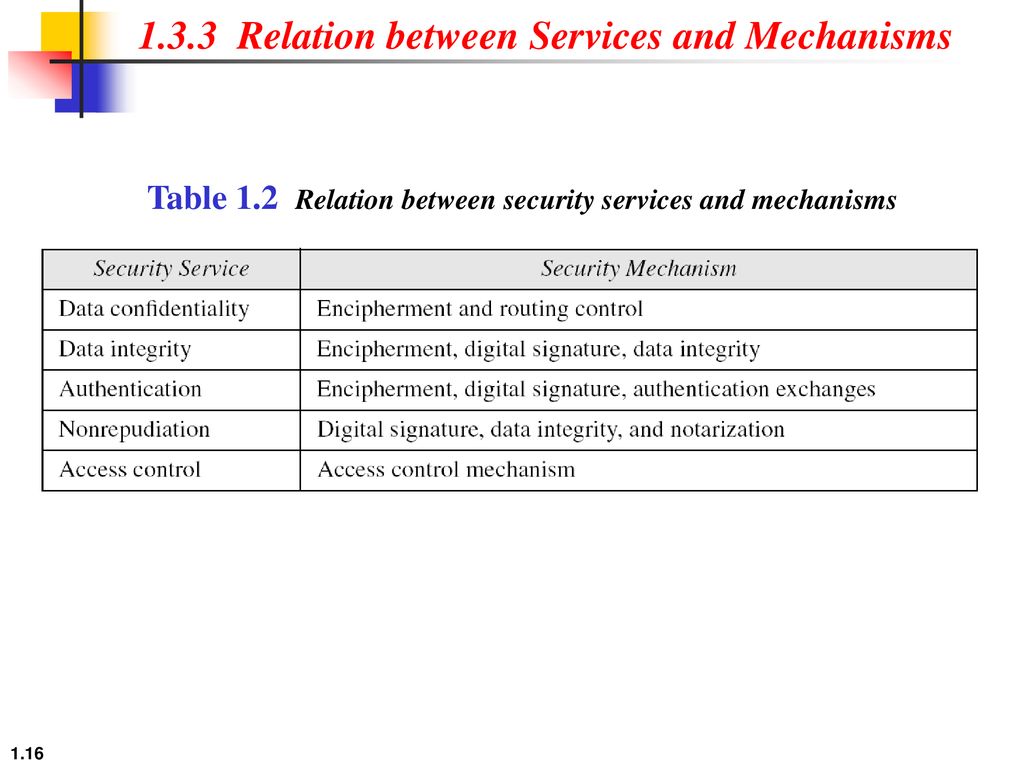
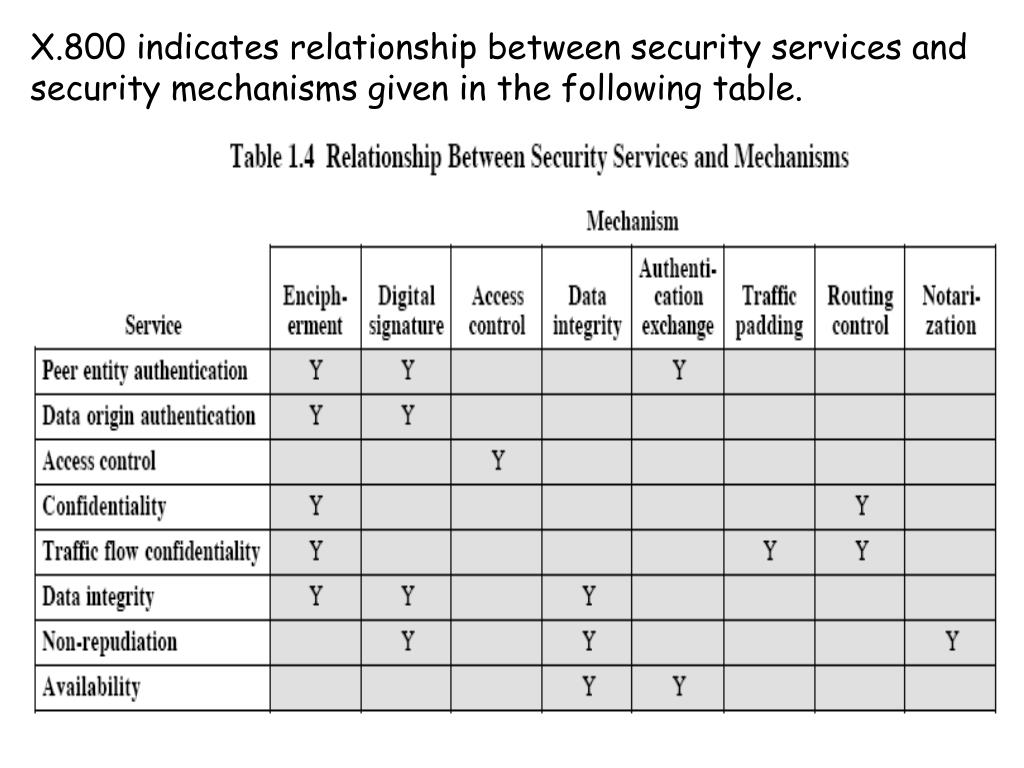
Chapter 1 Introduction Copyright © The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 1.# - ppt download